Securing the Open-Source Ecosystem:
How Runtime Reachability Helps with Vulnerability Management
By Ali Naqvi
Open-source and third-party packages are essential to modern software development. They drive innovation, significantly cut down development time, and are integral to the success of building applications. However, there are challenges that come with the open-source ecosystem. They introduce flaws that leave your application vulnerable to attacks.
Wouldn’t It be great if you could stop chasing ghosts in your codebase and focus on the vulnerabilities that matter? That’s where runtime reachability comes in. By determining if a vulnerability in your dependencies is exploitable in your application, runtime reachability changes how we secure open-source and third-party packages.
Open Source: A Double-Edged Sword
Open-source and third-party packages are powerful tools, but they often come with a lot of:
Noise in Vulnerability Scans. Static scans can overwhelm security teams with endless alerts, many of which are irrelevant.
Dependency Chaos: Vulnerabilities deep in the dependency tree are hard to spot and harder to prioritize.
Limited Context: Without runtime data, it’s nearly impossible to know if a flagged vulnerability actually impacts your application.
Traditional Software Composition Analysis (SCA) tools are excellent for identifying vulnerabilities, but they often leave developers asking: Do I really need to fix this? This is where runtime reachability can help fill the gap.
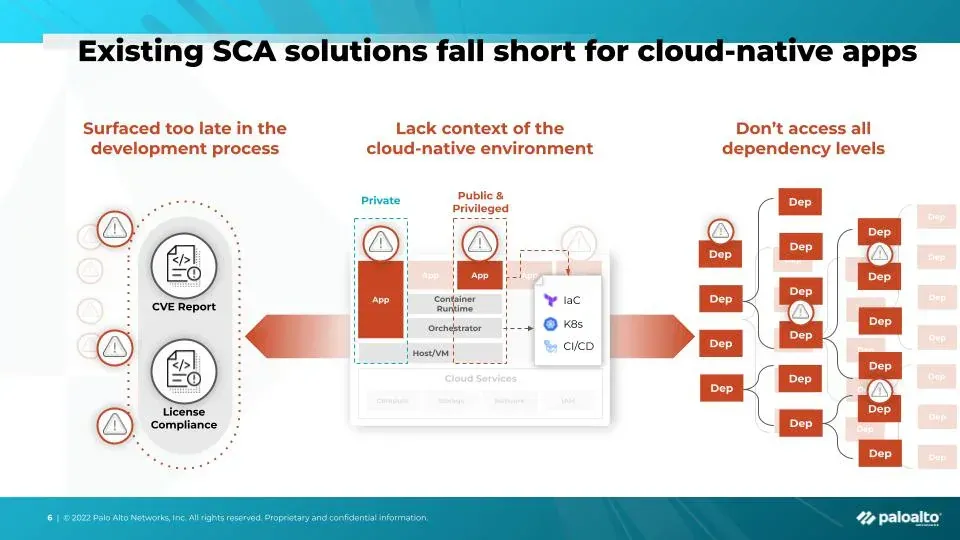
What is Runtime Reachability for Dependencies?
Runtime reachability is the ability to determine whether a flagged vulnerability in your open-source or third-party package:
1. Runs in Production: Does your application execute the vulnerable code?
2. Processes Input: Can user or system input trigger the vulnerability?
3. Is Neutralized: Are safeguards like authentication or input validation preventing exploitation?
By answering these questions, runtime reachability transforms vulnerability management from a time-consuming chore into a precise, focused process.
Imagine This Scenario:
Your app uses a popular data processing library. A vulnerability in a deprecated XML parsing feature is flagged by your SCA tool. You need to patch it now.
But wait! Runtime reachability analysis shows:
1. The XML feature isn’t used in your app.
2. None of your code paths reach the vulnerable function.
Instead of wasting time on a false positive, your team can focus on real threats and stay one step ahead of attackers.
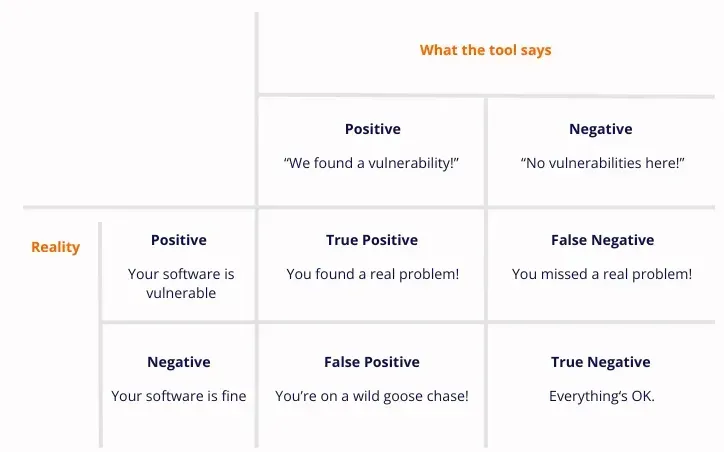
Runtime Reachability is the Game-Changer for Open-Source Security:
Here’s how runtime reachability solves some of the biggest pain points in dependency management:
1.
Filter Out the Noise: Reduce the number of alerts by focusing on the vulnerabilities that actually affect your app.
2.
Boost Team Productivity: Developers spend less time on false positives and more time fixing real issues.
3.
Better Security Posture: By fixing truly exploitable vulnerabilities, your app is more secure without unnecessary patches.
The Language Effect: Runtime Reachability and Ecosystems
Runtime reachability’s effectiveness depends on your language and its ecosystem.
1.
Java: The Enterprise Giant
Java’s JVM has excellent introspection capabilities, making analyzing runtime behavior easier. Tools can track complex dependency trees in frameworks like Spring so you can get precise vulnerability assessments.
2.
Python: The Dynamic Workhorse
Python’s flexibility comes with dynamic imports and many third-party packages. Runtime reachability shines here by telling you if pip-installed libraries' vulnerabilities are exploitable.
3.
JavaScript/Node.js: The Dependency Heavyweight
Node.js apps often have deep dependency trees via npm. Runtime reachability shows you which packages or modules are actually used. For instance, an unused route in Express.js has a vulnerability, but runtime analysis shows it’s not a problem.
4. Go (Golang): The Static Minimalist
Go’s static nature makes it easier to map vulnerabilities but limits runtime analysis depth. Runtime reachability can find reachable vulnerabilities, but Go’s predictable execution paths reduce the noise from static scans.

Turning Data into Action:
Open source is getting bigger; runtime reachability will be mandatory. It’s the missing link between static analysis and real-world risk, so developers and security teams can align without sacrificing speed or security. Runtime reachability lets you stop reacting to every vulnerability and make data-driven decisions. With fewer distractions from noise, your team can focus on code quality and speed.
Conclusion:
Open-source and third-party packages typically make up 70% of modern software applications. Managing vulnerabilities within these packages has significant challenges. Traditional static scans are helpful in detecting issues, but they often detect many false positives. Runtime reachability determines whether vulnerabilities are executed in production, reachable by user input, or mitigated by existing controls. This changes the way we can approach security in open-source ecosystems. It lets developers work more efficiently, reduces unnecessary patching, and strengthens application security.
As languages and frameworks change, runtime reachability will be key to adapting to the complexity of modern development. Whether working with Java’s enterprise frameworks, Python’s dynamic libraries, or Node.js’ dependency trees, runtime reachability gives you clarity and precision in vulnerability management.
In the end, the future of AppSec is combining traditional analysis with intelligent runtime insights. This way, you can protect your applications and make sure your security efforts are focused where it matters most – on the real-world risks that matter.










